Global Business Networking and The Hidden Dangers of Linkedin
1. Ethical concerns as a small (unverified) business owner
LinkedIn - “the world’s largest professional network”, boasts over “660+ million users in more than 200 countries and territories worldwide”, has the mission to “connect the world’s professionals to make them more productive and successful” and the vision to “create economic opportunity for every member of the global workforce”. It sounds wonderful, doesn’t it?
What LinkedIn doesn’t mention to its users, however, is that there’s no verification process in place to establish whether a business entity is (or isn’t) legitimate. I know because I’m a small business owner myself, and I was able to set up my own business page - filled with any information I saw fit - weeks before the registration process for Mudita Consultancy was completed. No proof of business needed.
So, here’s the steps involved in the creation of a business page works:
- choose a company name;
- confirm the LinkedIn public URL;
- tick a box to verify that YOU have the right to act on behalf of the company
Have you spotted the main problem with this procedure? That’s right, no proof of identity is needed either to set up a personal account.

Now, watch how from the business page of an entity LinkedIn failed to verify (page that, by the way, I access through a personal, free domain email address), I proceed to create a job post:
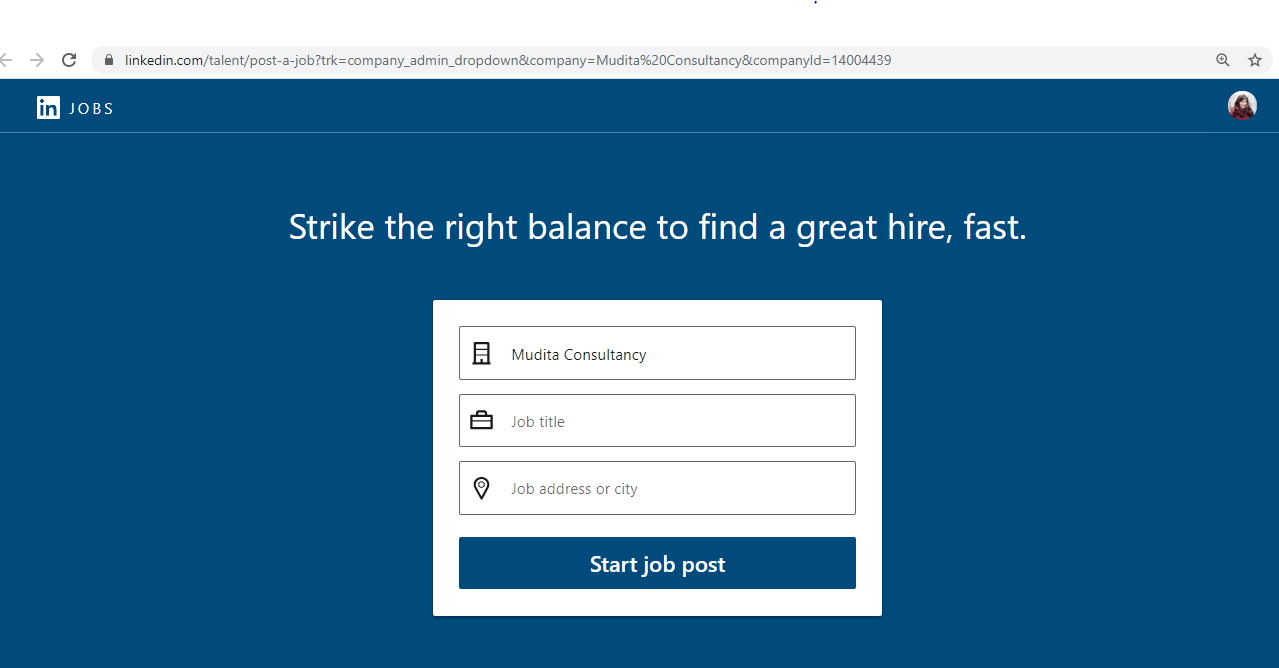

Finally, here’s how any company listed on LinkedIn - regardless of its legitimacy - can gain easy access to your data:
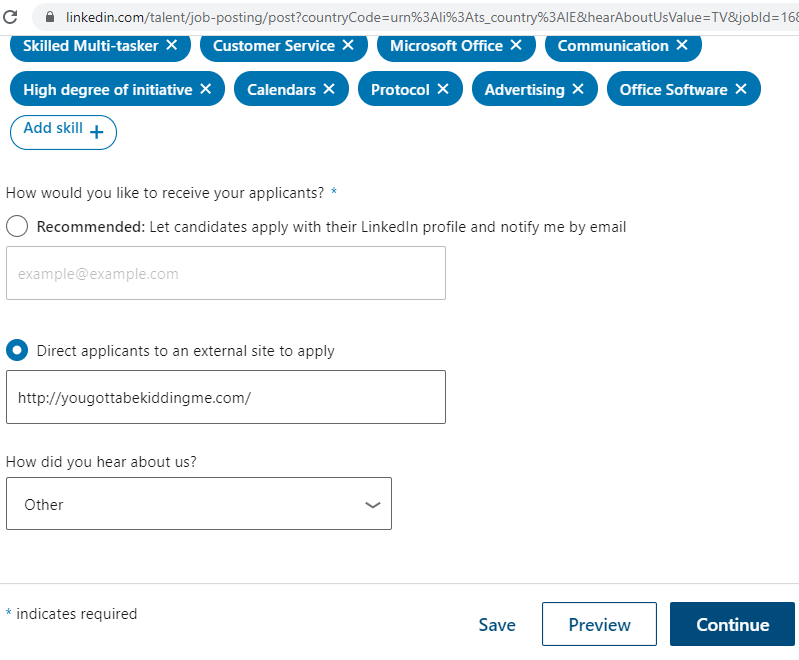
Now some numbers: for LinkedIn, the safety of its users is worth less than 20 € per day. The higher the budget, the higher the amount of resumes - and valuable data users may not otherwise be willing to share - a bogus organization will be able to collect.
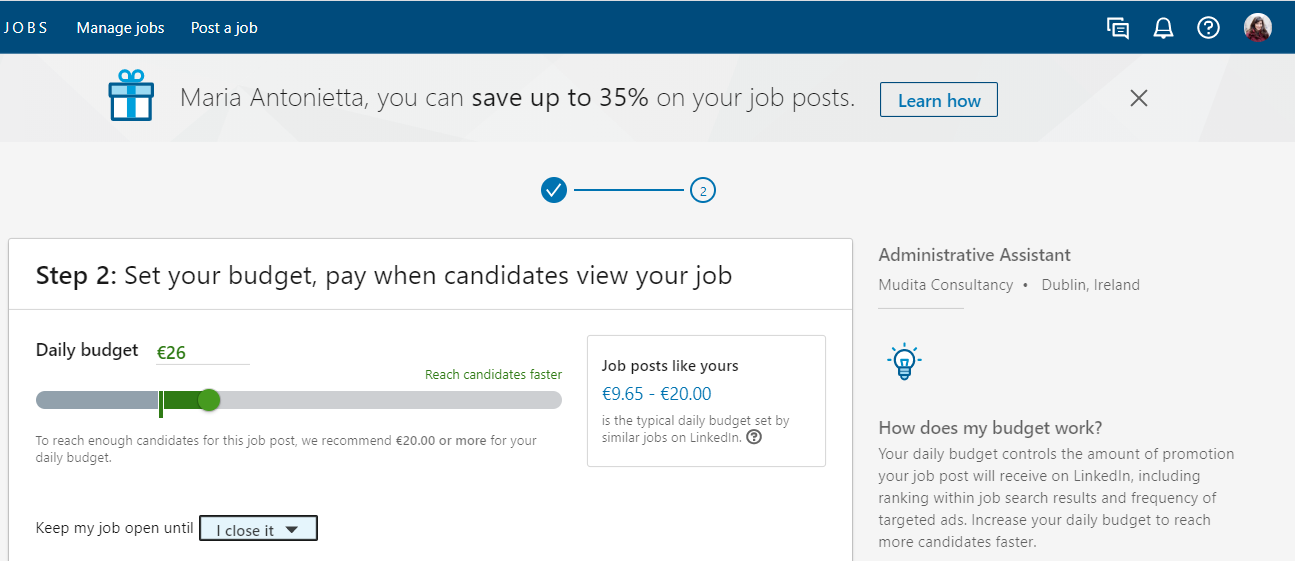
2. The jobseeker dilemma: to trust or not to trust?
A post shared on Symantec’s blog back in 2915 - “Fake LinkedIn accounts want to add you to their professional network” - claimed that “Scammers copy information from real LinkedIn profiles to pose as recruiters and attract new connections”, warned that “LinkedIn is a prime target for scammers looking to connect with professionals in a variety of industries”, and explained that “Using these fake LinkedIn accounts, scammers are able to establish a sense of credibility among professionals in order to initiate further connections. In addition to mapping connections, scammers can also scrape contact information from their connections, including personal and professional email addresses as well as phone numbers. This information could be used to send spear-phishing emails (for the difference between Phishing, Spear Phishing and Social Engineering see the related Graphus' blog post here)”
In the same year, an article published by Secureworks, reported that:
- “While tracking a suspected Iran-based threat group known as Threat Group-2889 (TG-2889), Dell SecureWorks Counter Threat Unit™ (CTU) researchers uncovered a network of fake LinkedIn profiles. These convincing profiles form a self-referenced network of seemingly established LinkedIn users”;
- “The 25 fake LinkedIn accounts identified by CTU researchers fall into two categories: fully developed personas (Leader) and supporting personas (Supporter). The table in the Appendix lists details associated with the accounts. The level of detail in the profiles suggests that the threat actors invested substantial time and effort into creating and maintaining these personas. The photos used in the fake accounts are likely of innocent individuals who have no connection to TG-2889 activity.”;
- “The purpose of the Supporter personas appears to be to provide LinkedIn skills endorsements for Leader personas, likely to add legitimacy to the Leader personas. As shown in Figure 5, most of the Supporter accounts identified by CTU researchers have endorsed skills listed on the profiles of the Leader personas. Although unable to view Leader personas' LinkedIn connections, CTU researchers suspect the threat actors use the Supporter accounts to provide the Leader profiles with an established network, which also enhances credibility.”;
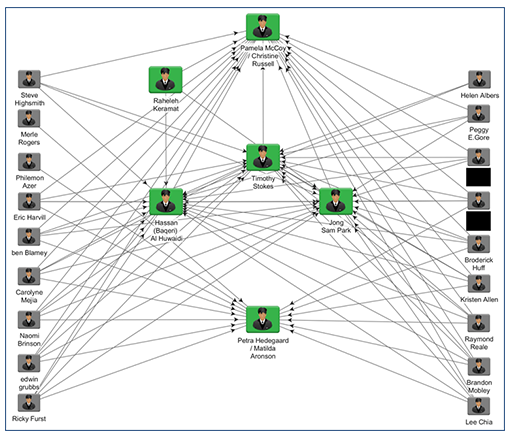
- “Five of the Leader personas claim to be recruitment consultants, which would provide a pretext for contacting targets. TG-2889 likely uses spearphishing or malicious websites to compromise victims, and established trust relationships significantly increase the likelihood of these tactics being successful”;
- “ Based on strong circumstantial evidence, CTU researchers assess that TG-2889 is linked to the activity that Cylance described in its December 2014 Operation CLEAVER report. The report documented threat actors using malware disguised as a resume application that appeared to allow resumes to be submitted to the industrial conglomerate Teledyne.”
See the first point of this article: anyone can easily gain access to your (actually, our) data, remember?

- “Updates to profile content such as employment history suggest that TG-2889 regularly maintains these fake profiles. The persona changes and job alterations could suggest preparations for a new campaign, and the decision to reference Northrup Grumman and Airbus Group may indicate that the threat actors plan to target the aerospace vertical. It is likely that TG-2889 maintains personas that have not yet been identified, and that other threat groups also use this tactic.”
It’s perhaps worth mentioning that “The attackers, dubbed ‘Threat Group-2889’ or ‘TG-2889,’ appear to be the Iranian-sponsored hackers whose activities were documented by endpoint security company Cylance in a December 2014 report focusing on a campaign called ‘Operation Cleaver’. The group behind Operation Cleaver has been active since at least 2012 and it has targeted more than 50 companies across 16 countries, including organizations in the military, government, oil and gas, energy and utilities, chemical, transportation, healthcare, education, telecommunications, technology, aerospace, and defense sector”.
But hey, that’s old news! It all happened in 2015 after all… You’d think that LinkedIn implemented some security measures after the reports were published, right? Wrong.
Have you ever met London-based photographer Mia Ash?

“In early 2017, SecureWorks Counter Threat Unit (CTU) researchers observed phishing campaigns targeting several entities in the Middle East and North Africa (MENA), with a focus on Saudi Arabian organizations. The campaigns delivered PupyRAT, an open-source cross-platform remote access trojan (RAT). CTU researchers observed likely unsuccessful phishing campaigns being followed by highly targeted spearphishing and social engineering attacks from a threat actor using the name Mia Ash. Further analysis revealed a well-established collection of fake social media profiles that appear intended to build trust and rapport with potential victims. The connections associated with these profiles indicate the threat actor began using the persona to target organizations in April 2016.”.
Different year, same story.
“On January 13, 2017, the purported London-based photographer "Mia Ash" used LinkedIn to contact an employee at one of the targeted organizations, stating that the inquiry was part of an exercise to reach out to people around the world. Over the next several days, the individuals exchanged messages about their professions, photography, and travels.”
Since in 2020 it is still possible to create business pages without any restrictions whatsoever, it would appear that LinkedIn has not learnt anything from the previous security issues that affected many of its users and hasn’t actually worked toward the implementation of a better, much needed verification process.
So, now what? How can users protect themselves on a platform that doesn’t properly verify its business entities? Perform your due-diligence, verify that the business is legitimate and watch for red flags.
Recruitment group Hays shared in an article (available here) a list of tell-tale signs of fake recruiters profiles:
1. They have a LinkedIn profile which has a low amount of connections;
2. They have large amounts of information missing on their profile;
3. They spell ‘jobs’ as ‘j0bs’ on their LinkedIn profile, or they use a picture with the text ‘jobs’, so they’re able to circumnavigate the LinkedIn filter;
4. They feature a free email address on their LinkedIn profile (e.g. @gmail.com or @live.com);
5. They offer you the job without so much as a phone interview;
6. They send you a job offer letter which looks unprofessional; bright imagery and font are frequent red flags;
7. The job offer doesn’t detail the skills required, or specifies basic skills;
8. They ask you to make a payment;
9. They offer you a lot more money than you know the position to be worth (you can check the typical salary for a role using Hays Salary Guide);
10. They seem a little over-eager to seal the deal
Let’s now look at a couple of suspicious profiles that seem to tick some of those boxes.
Mitul Desai is a Talent Acquisition Specialist who works for an agency called “HR Recruitment”, that never advertised any jobs on its business page.
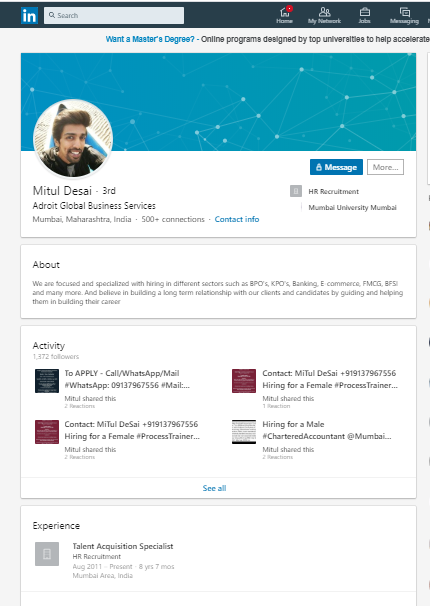
He uses a free email address (see 4th point of the above list), and also a picture with the text (3rd point), possibly in order to play the system as Hays suggests:
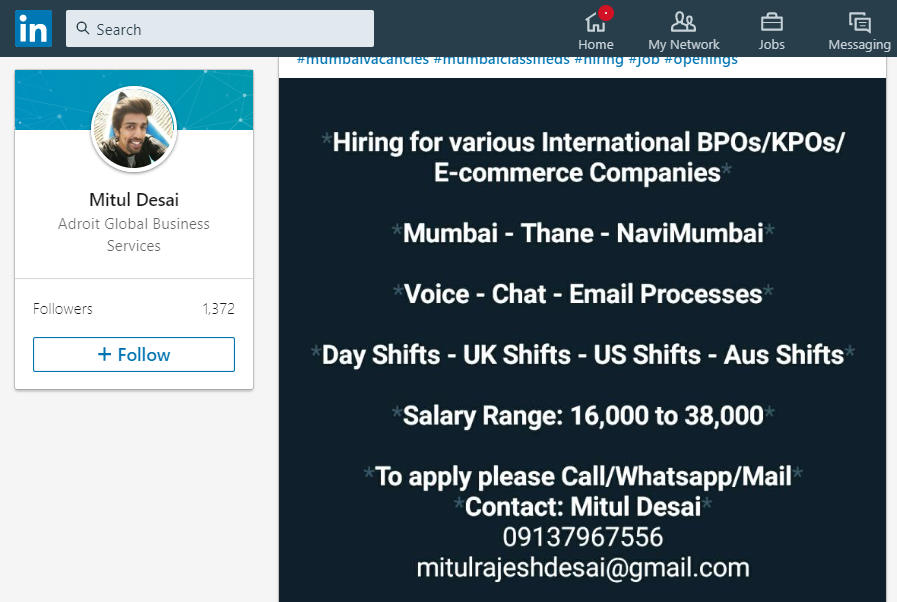
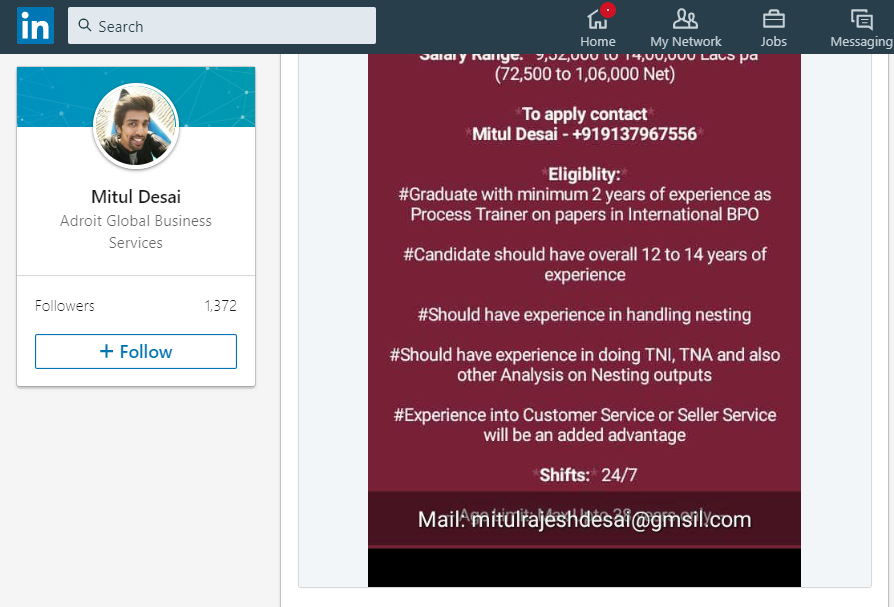
Things get especially awkward when “Mitul” (poorly) edits his email address, from [email protected] to [email protected], since the domain gmsil.com/ is actually owned by a legitimate US, Illinois based Company, Group Marketing Services.
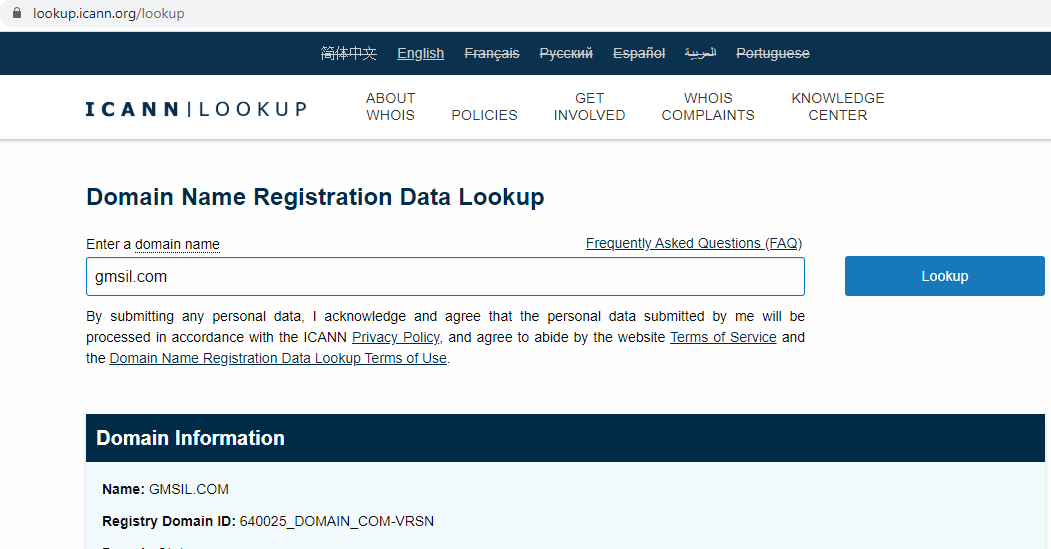
The domain owner (domain ownership can be checked here, https://lookup.icann.org/lookup, although some businesses - like my own - choose to keep the registration details private) seems to be another Illinois based Company, R. W. Garrett Agency, Inc.:
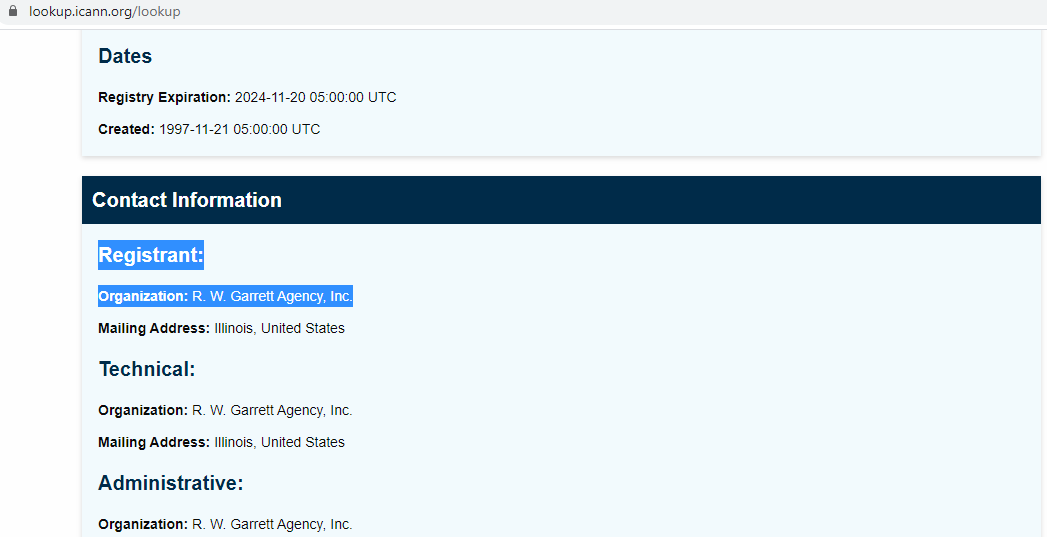
Note:
- Registrants are the people or businesses that own a certain domain name;
- Registrars are ICANN accredited organizations that have the authority to issue domain licenses to registrants;
- ICANN is the Internet Corporation for Assigned Names and Numbers;
But let’s go back to Mitul (or to the individual impersonating him) and to the Company he claims to work for.
The only thing we are able to discover about “HR Recruiment” is that its specialties include “HR Recruitment, developing interest towards Employer, fesilitate Employee, beneficial for career plan, and opportunities for better development” and that it employs 78 people.

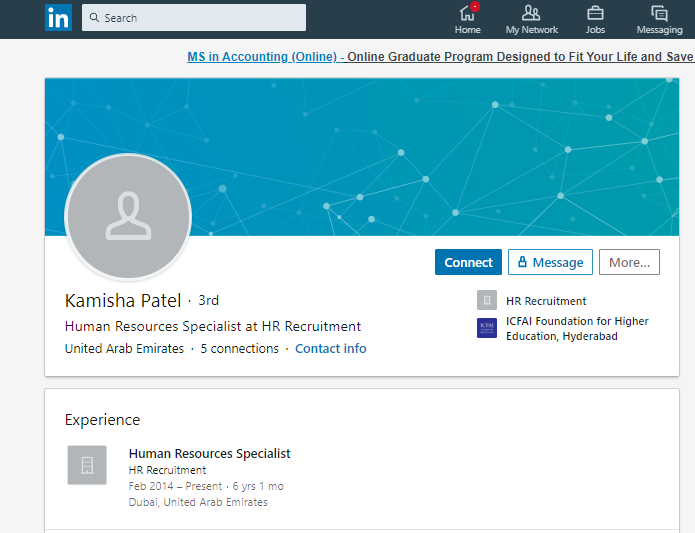
Who are these people then? They’re employees like Kamisha Patel, with no visible no activity, no photos, no details…
…or like Ruxandra Trif, again a profile with no visible no activity, no photos, no details, and many others.
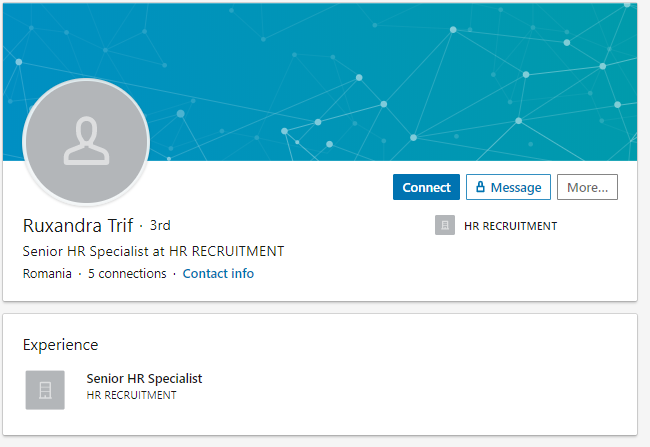
Have you noticed that both Kamish and Ruxandra are dormant accounts with five connections each? Maybe it’s a just a coincidence, but here’s what the previously mentioned Secureworks article claims about the Supporter Personas: “Profiles for Supporter personas are far less developed than for Leader personas. They all use the same basic template with one simple job description, and they all have five connections ”.
Let’s now try to find out whether Mitul does actually work for a legitimate organization whose only faults are an incredibly vague and generic business name and a poorly maintained LinkedIn business page: according to the latter, “HR Recruitment” is a company based in Karachi, Pakistan.
The company register (“an official list of all the companies in a country, together with information about them, copies of their accounts, etc.”) for Pakistan is SECP, The Securities and Exchange Commission of Pakistan.
The legitimacy of local business entities can be checked here:
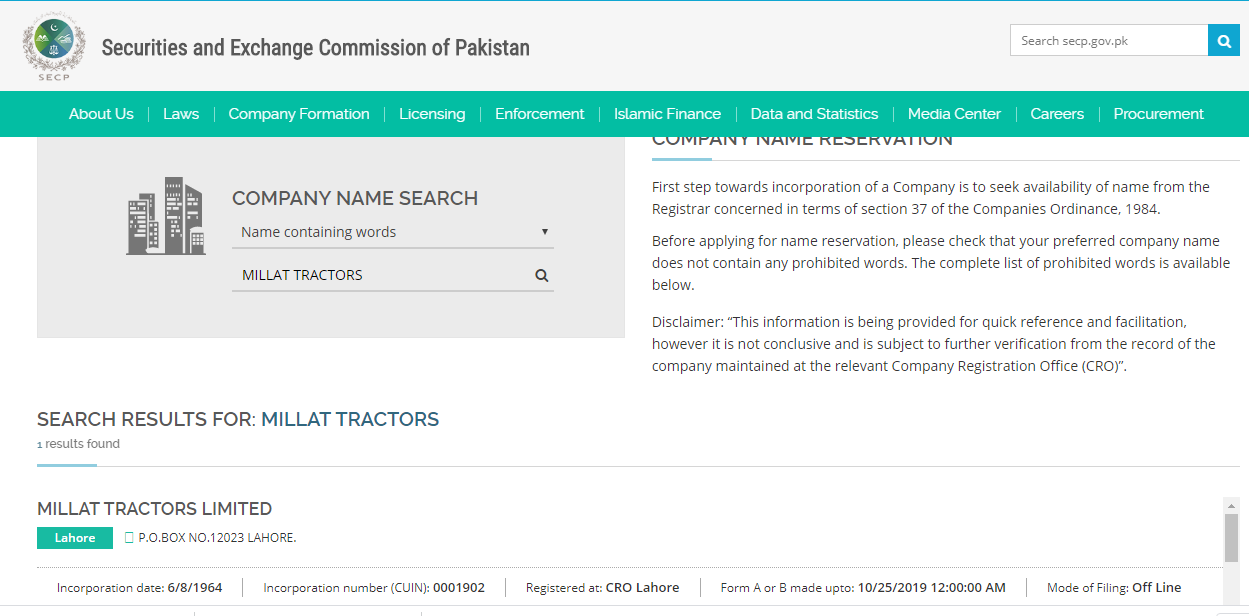
- https://www.secp.gov.pk/company-name-search/
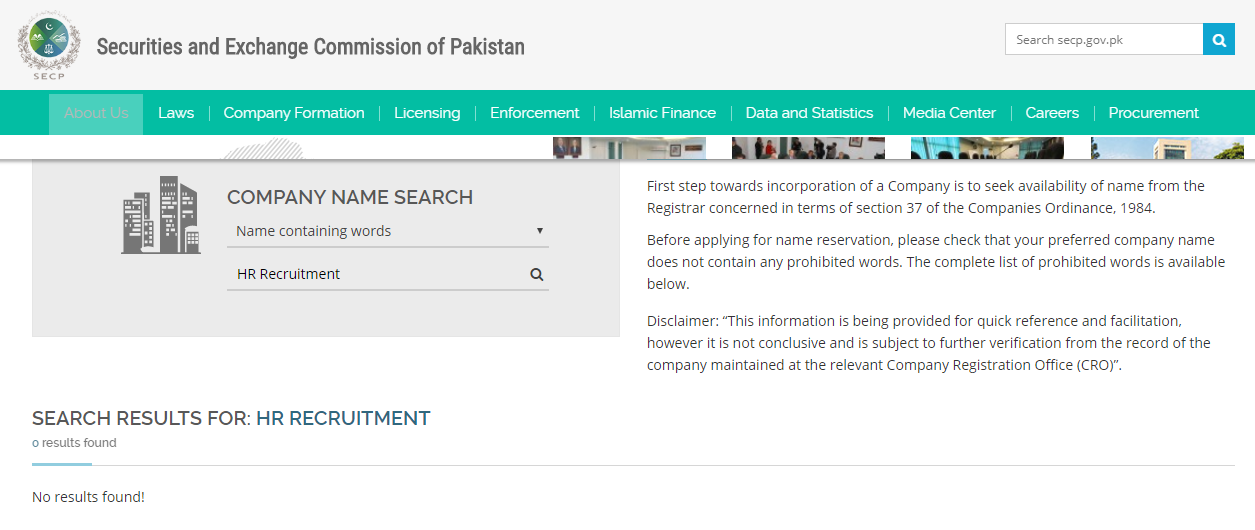
As you can see, nothing comes up when we look for a company called “HR Recruitment”. If the business was a legitimate, officially registered entity such as (for example) “Millat Tractors Limited”, the outcome would be significantly different:
What else looks slightly suspicious about Mitul’s account?
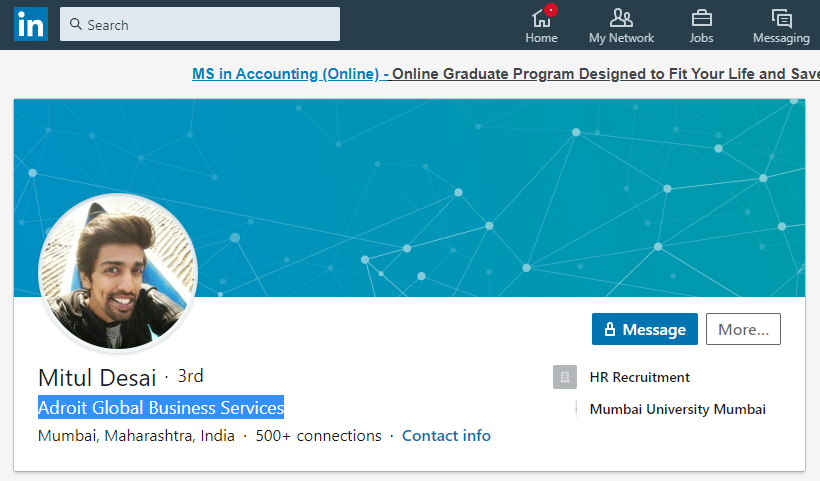
While he claims to work for a Pakistani organization, his headline reads “Adroit Global Business Services”, “Mumbai, Maharashtra, India”.
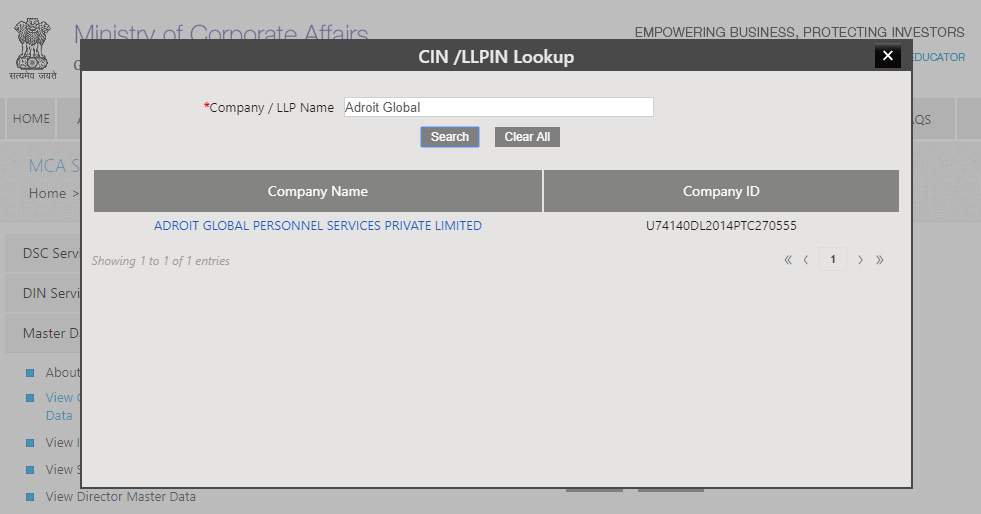
The company register for India is the Ministry of Corporate Affairs. Business entities can be verified here: http://www.mca.gov.in/mcafoportal/viewCompanyMasterData.do

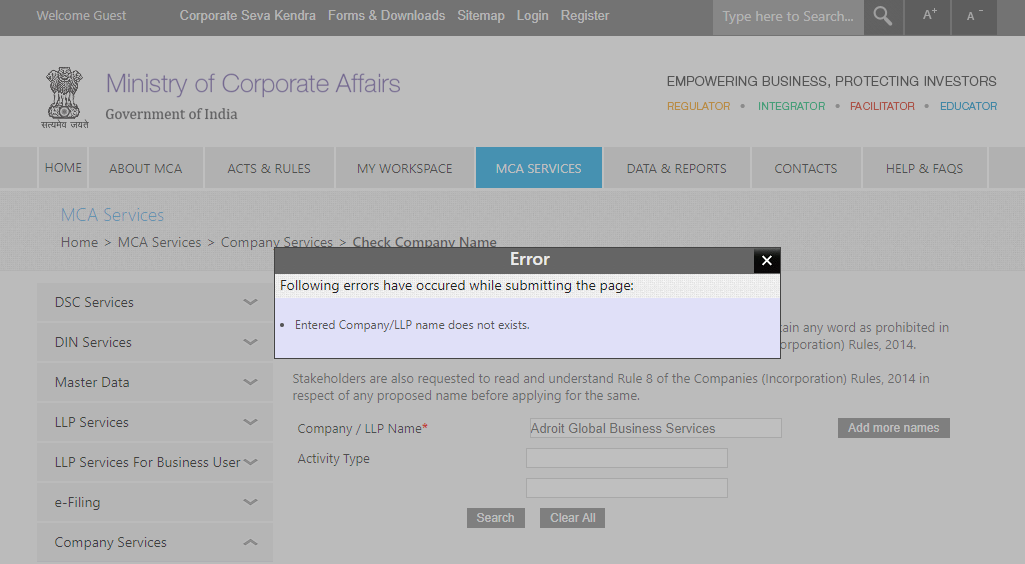
If we look for “Adroit Global”, the research returns one single result: a company called “Adroit Global Personnel Services Private Limited”, based in Delhi.

No company registered as “Adroit Global Business Services” seems to exist.
What about 2019? Was the issue with fake accounts addressed by then?
Not quite. According to cybersecurity firm FireEye, “In late June 2019, FireEye identified a phishing campaign conducted by APT34, an Iranian-nexus threat actor. Three key attributes caught our eye with this particular campaign:
- Masquerading as a member of Cambridge University to gain victims’ trust to open malicious documents;
- The usage of LinkedIn to deliver malicious documents;
- The addition of three new malware families to APT34’s arsenal.
Managed Defense reached out to the impacted customer’s security team, who confirmed the file was received via a LinkedIn message. The targeted employee conversed with ‘Rebecca Watts’, allegedly employed as ‘Research Staff at University of Cambridge’. The conversation with Ms. Watts began with the solicitation of resumes for potential job opportunities.”
In the meantime, while LinkedIn struggles to catch up with fraudulent trends, platforms like Upwork have whole sections dedicated to business documents and account verification:
"UTG (Upwork Talent Group) must determine whether you qualify as an independent contractor for each project (also known as worker classification). To make this determination, the Upwork compliance team reviews details regarding the project and your business. Depending on the scope of the project, Upwork may ask you to submit information to confirm that you’re self-employed and otherwise running your own business—especially if you’re new to using Upwork.."
"Some clients may require confirmation that you operate as a business before you can start a contract. On Upwork, these include certain Enterprise contracts, and you may be asked to provide confirmation in advance of receiving a contract (e.g., when you submit a proposal), so you’re ‘Enterprise Ready’ when you do win a contract.
The good news is that as a freelancer on Upwork, you’re operating as a business, even if it’s only in a sole proprietor basis. Plus, there are benefits for establishing a business entity (see here for what’s right for you).
But freelancing on Upwork may not be enough to prove you are a business for every project.
Here are some ways you can show you have a business
-
Business license
-
Proof of status as a limited liability company (LLC), corporation, or other entity, such as articles of organization, certificate of incorporation, or online registration summary
-
Proof of registration with any tax, social security or other agency as an independent contractor, sole trader, private entrepreneur, or other self-employed individual
-
Proof of registration of a business name (dba), such as a fictitious business name statement, registration of trade name, or certificate of assumed name
-
Form or notice showing your U.S. Employer Identification Number (EIN) or international business tax number
-
Certificate of Insurance or other proof of liability insurance
-
Proof that you have unemployment or workers’ compensation insurance
-
Invoices to other clients within last 12 months
-
Business tax return (e.g. Schedule C from U.S. Form 1040)
-
Commercial office space lease
-
Coworking space membership or lease
-
Proof of payrolling yourself or hiring employees or freelancers for your business
Note: Your documents may be redacted at your discretion to remove sensitive information, but please leave enough details so that Upwork can still review the document.”
See the difference between a platform committed to offering a safe, controlled environment to its users, and one that’s mostly committed to granting free access to anyone for the purpose of becoming “the world’s largest professional network” at the expenses of its users?
3. When everything else fails, Do It Yourself
Company Registers (Business verification)
If and when in doubt about the legitimacy of a business account (as highlighted in the previous section, a seemingly established account, a large network, and a business website are unfortunately not truly indicative of anything), it would be advisable for LinkedIn users to perform their own background checks.
A list of global company registers can be found here (note: some of them are not available in English), or alternatively here (examples of how to use the registers for India and Pakistan were provided in the previous section). For the Euro-zone specifically, see the list below (kindly compiled by Alessia (Blasi) Bräutigam, Senior Compliance Training Specialist and Cybercrime Expert):
Domain Verification:
Domain ownership, unless the registrant (owner) chose to keep those data confidential, should provide you with a number of potentially useful information.
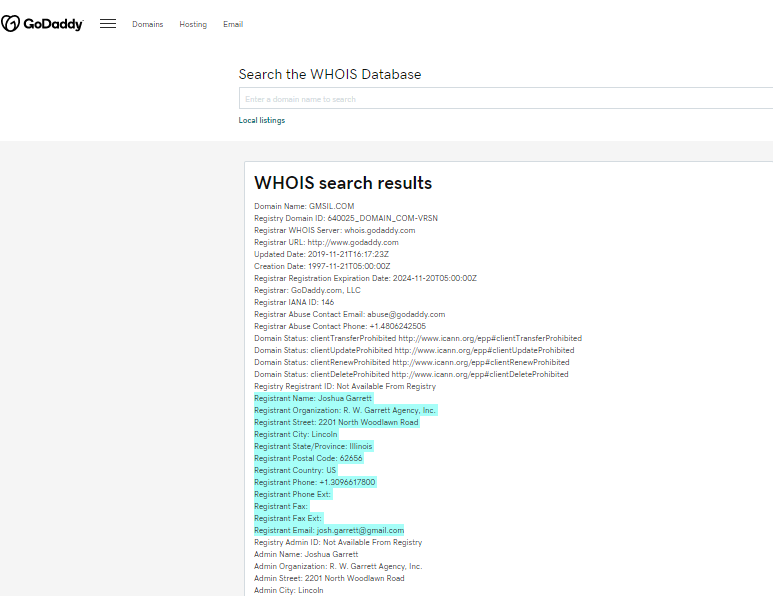
Do you remember how we’ve discovered that the domain gmsil.com used by a presumably fake Pakistani recruiter belongs to an Illinois based company, R. W. Garrett Agency, Inc?
What sort of information can I find through a quick WHOIS search?
GoDaddy indicates that the domain was created in 1997 and shows the same address details listed on the company website (2201 North Woodlawn Road, Lincoln, IL 62656), factors that suggest both stability and reliability.
Some of the most common WHOIS domain lookup tools are:
- http://whois.domaintools.com/
- https://www.eurodns.com/whois-search/best-domain-name
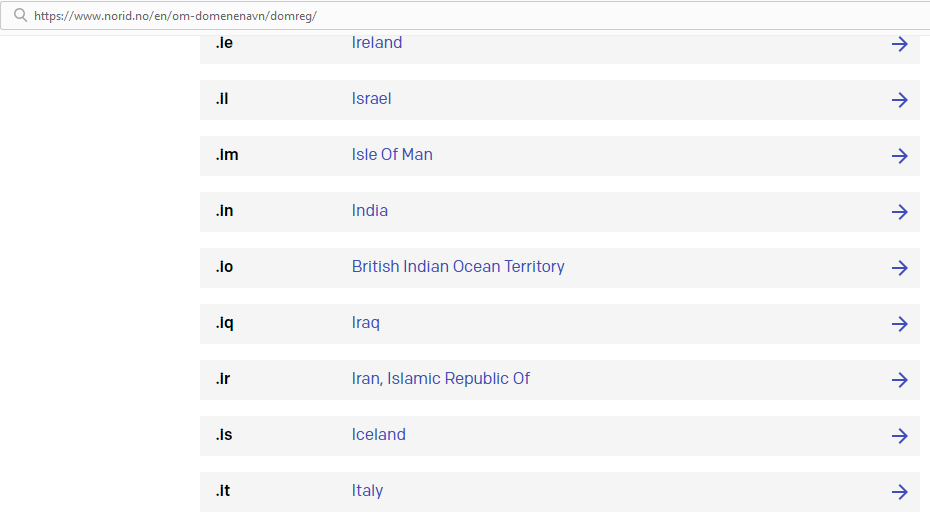
For Country Code Top Level Domains, go to the following page and click on the Country extension of the domain you wish to check:
https://www.norid.no/en/om-domenenavn/domreg/
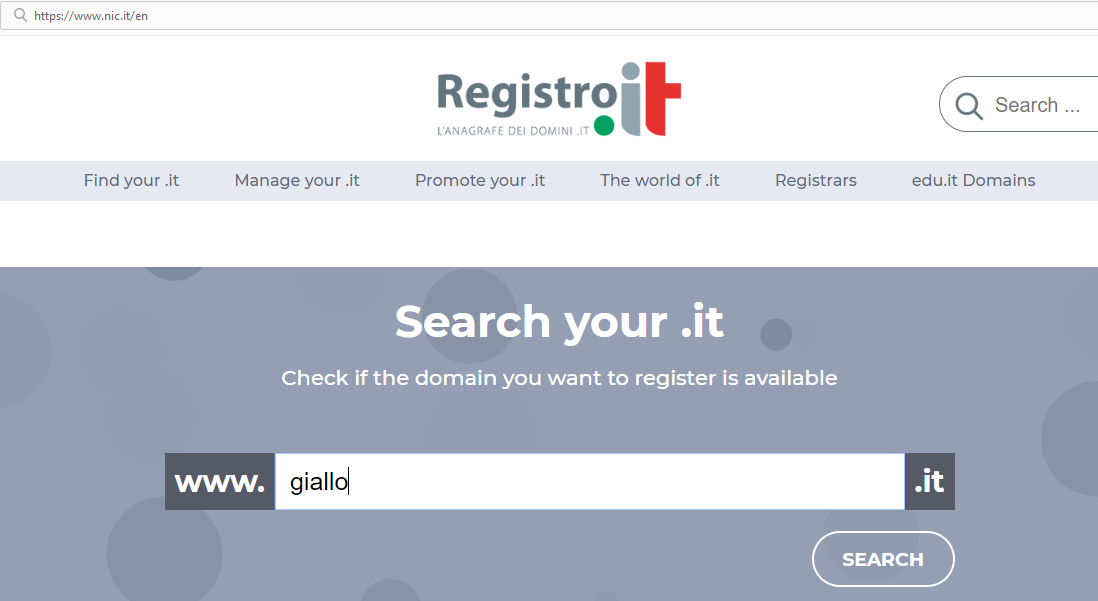
If, for example, you’re interested in knowing who own the domain giallo.it, select the .it extension:
The fill in the blank field, and hit Search:
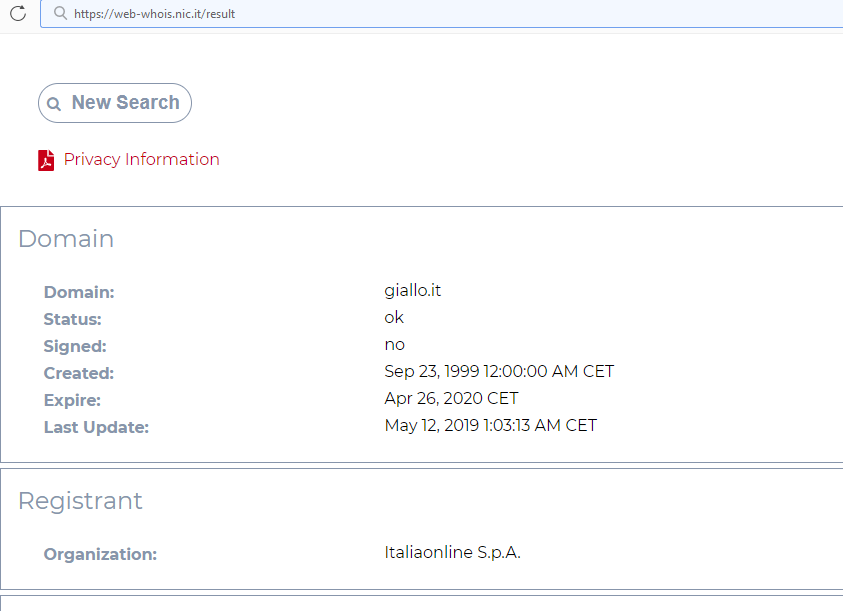
The domain giallo.it is owned by an organization called Italiaonline S.p.A.:
Finally, if we wish to cross- or double check the domain registration info, let’s go to the business register for Italy, Portale Infoimprese:

Note: the Portal is available exclusively in Italian. “Regione, Sigla Provincia, Comune o CAP” (Region, province, town, postcode) are the geographical references, if known.
The search conducted by the name of the company returned one result:

By clicking on “Visualizza”, you’ll be able to find the legal address (or addresses) of the organization:

******
Please feel free to get in touch if you have any questions or doubts about any of the topics covered in this article, and let me know if you’d be happy to read further posts about the complicated bureaucracy of international business (a comment to this post will do :)

